The OWASP Top Ten – what it is and isn’t
What is the OWASP Top Ten, and - just as important - what is it NOT? Let's explore how you can make it work for you.

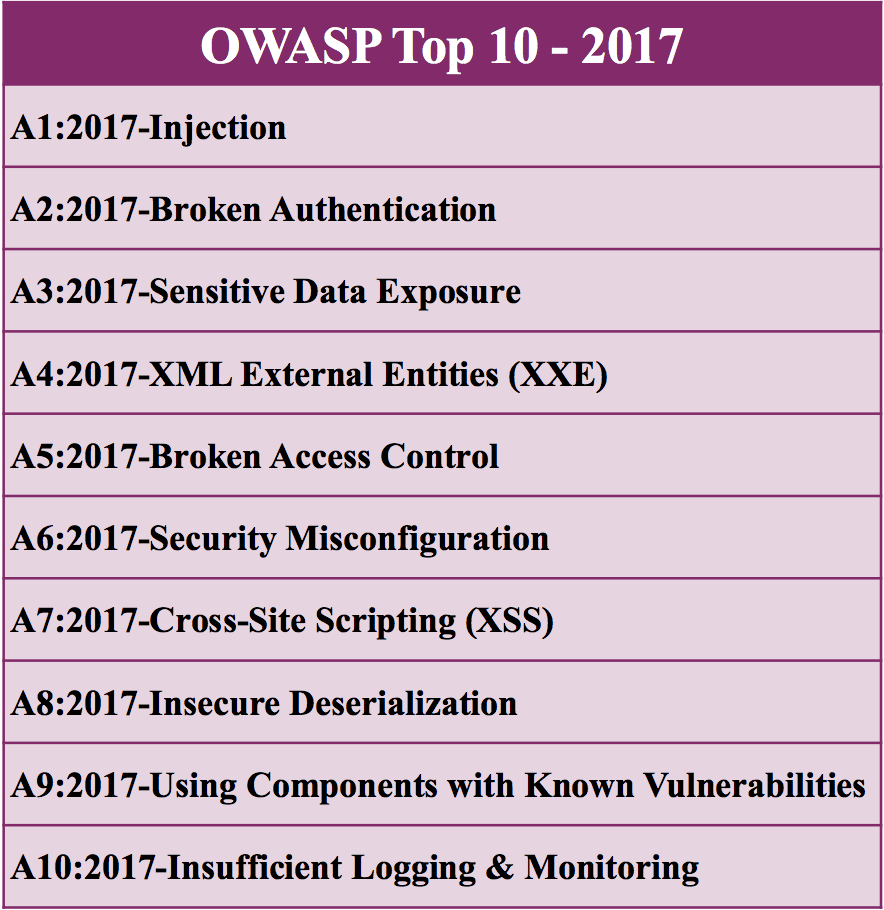
The OWASP Top Ten is perhaps the best-known product of the Open Web Application Security Project – a document that summarizes that ten most critical security issues in web applications to raise awareness and help minimize the risk of attacks. It is updated every 3 years (usually – e.g. it took 4 years between the 2013 and 2017 version) to keep pace with changes in the threat landscape and technology in general. It is updated every 3 years (usually – e.g. it took 4 years between the 2013 and 2017 version) to keep pace with changes in the threat landscape and technology in general.
What’s on OWASP Top Ten list?
Originally, the OWASP Top Ten was created via a data call, asking several communities – security evaluators, security tool developers, and software vendors themselves – about the incidence of each vulnerability type. The team then picked the ten most commonly found (highest incidence) security issues and performed a risk analysis to put them in a top 10 list.
The OWASP Top Ten in 2017, they used a different approach – while 8 of the 10 items would still be gathered based on data from the call, they also surveyed 500 security experts to identify 2 ‘forward looking’ issues that may not be particularly common currently but are expected to become critical issues soon.
Release Candidate 1 of the Top Ten 2017 met with some criticism, as several security experts disputed the ‘Insufficient Attack Protection’ entry – claiming it was a vehicle for security software vendors to sell web application firewall and IDS software while not actually increasing the security level of the application; there were also arguments that the entry was not an actual application-level risk, but rather the missing implementation of a control. This controversy also forced the reorganization of the OWASP Top Ten project leadership, and the redesign of this entry into ‘Insufficient logging and monitoring’ (one of the forward-looking issues) in the final release of the Top Ten.
What can and can’t it do?
The OWASP Top Ten is great at helping spread awareness by providing basic information about the most critical security issues concerning web applications; and honestly, most of these issues apply to desktop, server, or embedded applications just as well.
Another advantage is observing trends by comparing the list and position of the entries to earlier versions of the OWASP Top Ten. It is obvious, for instance, that “Injection” is number one and is likely to remain there for quite some time as the vulnerability is technology- and platform-agnostic, produces syntactically-correct code, is unlikely to be discovered during functional testing, affects a large number of potential targets, and is caused by a programmer misunderstanding.
Finally, it is useful to security testers and evaluators by providing risk values for each entry. This helps in triage and prioritization of issues: a command injection vulnerability should be addressed before dealing with an inadequate logging implementation.
As the OWASP Top Ten is one of the best-known application security documents, it may be tempting to look at it as a standard, or even a compliance goal. However, keep in mind that the list is incomplete by design, and just making sure that none of the ten risks apply to your application does not guarantee its security; in fact, according to some vendors, up to 90% of all web applications may have at least one vulnerability not present in the Top Ten based on the analysis of the 2017 data call!
Make the OWASP Top Ten work for you
While the Top Ten started as purely a list of vulnerabilities, it has gradually moved towards security risks concerning web applications in a holistic sense – some of those risks are not necessarily programming bugs, such as “Sensitive Data Exposure”. There is a definite push towards devops with a look at security issues that come from the environment rather than the application code – there are now a total of 3 such risks in the Top Ten (“Security Misconfiguration”, “Using Components with Known Vulnerabilities” and “Insufficient Logging & Monitoring”).
All in all, the OWASP Top Ten is very useful as a primer on the most critical security issues for web applications today, as well as a way to keep up with changes in the threat landscape. However, to go deeper, the Application Security Verification Standard (ASVS) will give much better results, and a more thorough approach for security assurance of your web application.
While we cover a lot more than just the OWASP Top 10 in our training material, they make up the backbone of our courses such as Web application security in Python. And in our Web application security testing courses, we cover much of the ASVS to help the security testing team find all of these problems before it’s too late.