Cyber security from a galactic viewpoint
Security can mean a lot of things. Let's take a galactic view at cyber security and its implications to your products!

Cyber– as a prefix denotes words that are related to or are involving computer systems. Specifically, cyber security is all about the security of computer systems: their services and the data stored in them.
But what is security?
If a computer system is robust, it is both secure and safe: it means that the system is capable of performing without failure under a wide range of conditions. Put another way, things cannot go wrong neither by chance (which is safety: functional problems caused unintentionally, governed only by Murphy’s laws), nor by intention (which is cyber security: attacks caused by intelligent actors with malicious intent). In this sense robustness is the common denominator between security and safety.
The many faces of cyber security
Depending on the domain and scope, there are various types of cyber security. It is worthwhile to look at this closer, as in many cases one or the other type is simply taken as the definition of cyber security. In reality, cyber security has many faces, as shown in the figure below.
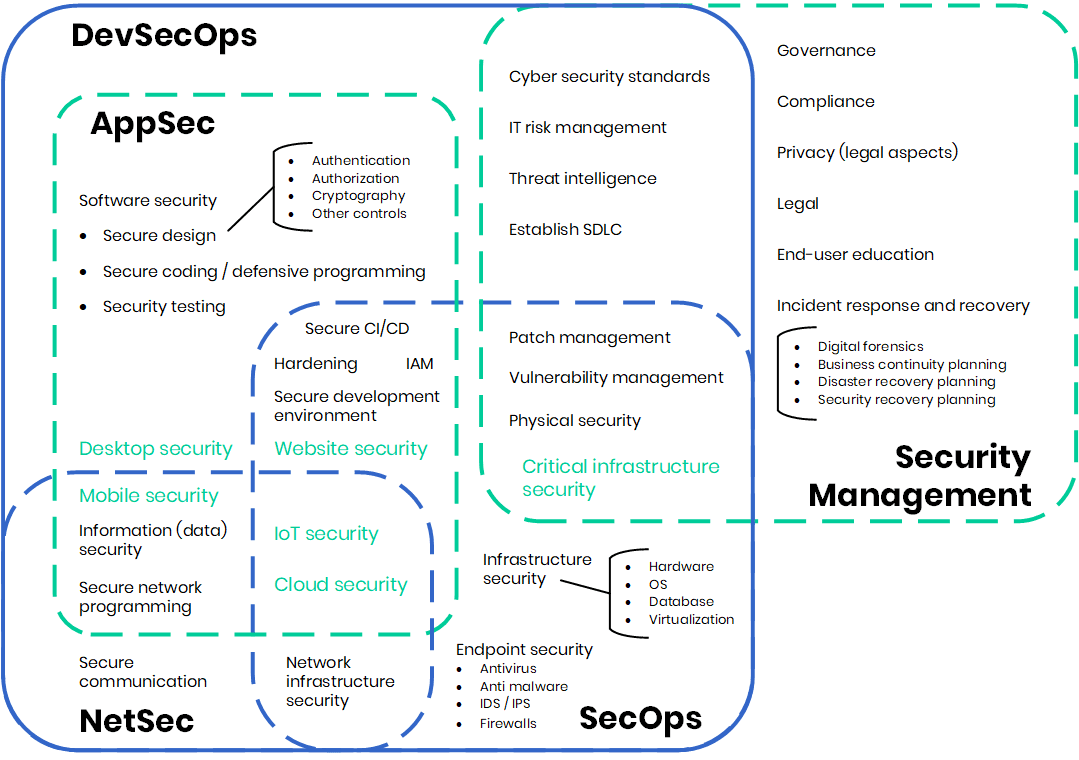
Network security
Network security (NetSec) is the practice of protecting the network infrastructure from malware, both from targeted ones and general attacks such as viruses. Disciplines include secure communications, the protection of the network infrastructure, as well as the secure implementation of the network nodes on all layers of the OSI model or the TCP/IP stack. It is especially relevant when we are talking about the cyber security aspects of networked devices, mobile platforms, and the cloud.
Application security
Application security (AppSec) is about the best practices to design, implement and deploy applications (Web, desktop, mobile, cloud, IoT devices) in a way to ensure confidentiality, integrity and availability of their data and services.
As part of this, information security (or data security / data protection) is concerned about the confidentiality of the data. This entails data at rest (file systems or databases), in transit (communication line, see Network security above) or in use. If the data is about someone, we call this privacy, which has many legal aspects as well – just think about GDPR.
Essential controls are access control solutions for data at rest, and cryptographic solutions in general. This entails symmetric or asymmetric encryption for confidentiality, and digital signatures or message authentication code for integrity.
But what about data in use? Well, software security, including secure design, secure coding practices (some call it defensive programming) and security testing are all about (eliminating) weaknesses and bugs that lead to vulnerabilities. There are well-known best practices in this domain – some of them decades old – but not many developers use them. That’s why code hygiene should be made a second nature, and developers should be taught how not to code. This aspect of cyber security is relevant for all software products – after all, everything is based on code.
Operations security
Once the application has been deployed, operations security (SecOps) is responsible for protecting assets in production. Concerns range from physical security and infrastructure security to endpoint security. Most commonly related controls are the authentication and authorization of users and connected systems implemented through access control or Identity and Access Management (IAM). This aspect of cyber security focuses on proactive measures to protect against threats. In the modern context of DevOps, it can combine with AppSec and NetSec concerns to form DevSecOps, building security into all steps of development.
Security management
Related disciplines include risk management, threat intelligence, governance, legal issues, secure development life cycle, etc. – it’s all about developing and implementing procedures and policies for protecting the assets. It is an aspect of cyber security that is important for the company rather than the product.
An essential part of security management is incident response and recovery. Business Continuity is the highest level aspect here; it can be broken down to Disaster Recovery Planning and Security Recovery Planning. The former is loosely connected to business continuity, while the second is focused on protecting the assets in case of an incident.
So, what is cyber security?
Cyber security is not just network security; neither is it solely secure coding, secure operation, or compliance with policies and standards. It’s the sum of all the above aspects; a complex beast that is hard (but not impossible!) to handle. One should understand its complexity in its entirety to be able to tackle all its aspects in a holistic way. Remember, a system is only secure as its weakest link.
Similarly, from organizational point of view security is a team sport: just as you cannot stop crime by putting a cop on every corner, you cannot ensure cyber security by having a security expert in each of the teams. It is the teams’ average preparedness that counts, so each and every developer should not only be aware of the problems and the risks, but should have the appropriate skills to produce reliable, robust and secure software.
It’s not rocket science – it’s all about the best practices after all. To help you with this, we are covering the basics of cyber security in all of our courses.